How to Solve Errors: "Subject Alternative Name Missing"; “NET::ERR_CERT_COMMON_NAME_INVALID”; or "Your connection is not private" in Google Chrome
-
Web Browser:
- Google Chrome Version 58 or higher
-
Epson Products:
- TM-T88VI-i / TM-T88VI-iHub
- TM-m30
- TM-P80 / TM-P60II / TM-P20
- UB-E04 / UB-R04
The problem:
For Chrome 58 and later, only the subjectAlternativeName extension (not commonName), is used to match the domain name and site certificate. If the certificate does not have the correct subjectAlternativeName extension, the user will receive an error warning that the connection isn’t private.
Background:
RFC 2818 describes two methods to match a domain name against a certificate:
- Using the available names within the subjectAlternativeName extension; or,
- Use the the commonName.
Use of commonName was deprecated in RFC 2818 (published 2000), but support remained in most clients. For security reasons, this support has now been removed.
Solutions:
Two options exist for Google Chrome users to work around this issue:
-
Disable the checking of subjectAlternativeName in Chrome.
This is a work-around that will not function beyond version 65 of Google Chrome, and should only be used a temporary fix.
-
Replace the offending certificate with one that uses the subjectAlternativeName extension.
If implemented correctly, this is a permanent fix that should work for most or all browsers that may implement subjectAlternativeName checking.
How to disable the checking of subjectAlternativeName in Chrome:
By adding the following setting to your environment, Chrome can be forced to allow certificates that are missing the subjectAlternativeName extension:
-
Windows registry (REG_DWORD):
Software\Policies\Google\Chrome\EnableCommonNameFallbackForLocalAnchors
-
Mac/Linux preference name (Boolean):
EnableCommonNameFallbackForLocalAnchors
-
Android restriction name (Boolean):
EnableCommonNameFallbackForLocalAnchors
When this setting is enabled, Google Chrome will use the commonName of a server certificate to match a hostname if the certificate is missing a subjectAlternativeName extension, as long as it successfully validates and chains to a locally-installed CA certificate.
|
|
|---|
|
A registery key can be added to Windows by entering the following at the Command Prompt: reg add HKLM\Software\Policies\Google\Chrome /v EnableCommonNameFallbackForLocalAnchors /t REG_DWORD /d 1 This workaround will cease to work beyond version 65 of Google Chrome. |
Example creation and upload of a certificate using the subjectAlternativeName extension
For this example, we will create a configuration file containing the required information:
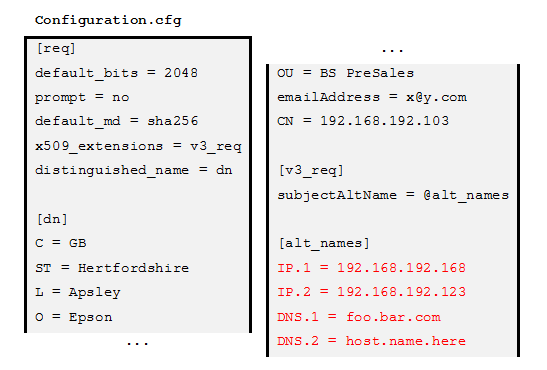
This file contains the specific details relating to the security objects we wish to generate, including the host names, highlighted in red. Notice that this can be an IP address, or DNS.
Once this file has been generated, we can run req to generate the security objects. For example:
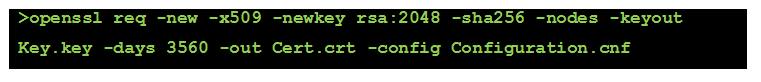
To be able to upload this the the printer, it is necessary to package the security objects (key and certificate) in a PKCS#12 archive. For example:
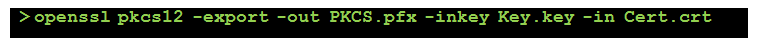
OpenSSL will interactively prompt for a password.
The result is a PKCS#12 archive ready to be uploaded to the server (printer), and a certificate ready to be installed in the client.